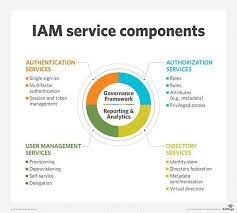
Identity and Access Management (IAM) is a critical component of cybersecurity infrastructure for businesses and organizations of all sizes. IAM refers to the processes, technologies, and policies used to manage digital identities and control access to resources within an organization’s IT environment. The importance of IAM cannot be overstated, as it plays a crucial role in safeguarding sensitive information, protecting against data breaches, and ensuring regulatory compliance.
1. Security and Data Protection
One of the primary reasons for implementing IAM is to enhance security and protect sensitive data from unauthorized access. By centralizing the management of user identities and access privileges, IAM solutions help organizations enforce security policies, authenticate users, and control access to critical systems and resources. This reduces the risk of unauthorized access and helps prevent data breaches and insider threats.
2. Regulatory Compliance
IAM solutions are essential for ensuring compliance with regulatory requirements and industry standards related to data privacy and security. Regulations such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS) mandate strict controls over access to sensitive information. IAM helps organizations meet these requirements by providing audit trails, enforcing access controls, and ensuring accountability for user actions.
3. Improved Productivity and User Experience
Effective IAM solutions streamline access management processes and provide users with seamless and secure access to the resources they need. Single sign-on (SSO) capabilities allow users to access multiple applications and systems with a single set of credentials, reducing the need for multiple passwords and improving productivity. Additionally, self-service capabilities enable users to reset passwords, update profiles, and request access permissions without IT intervention, further enhancing the user experience.
4. Risk Management and Mitigation
IAM solutions help organizations identify and mitigate security risks associated with user access rights and privileges. By implementing role-based access control (RBAC) and least privilege principles, organizations can ensure that users have access only to the resources necessary for their roles and responsibilities. This reduces the risk of insider threats, privilege misuse, and unauthorized access, thereby strengthening the organization’s overall security posture.
5. Scalability and Flexibility
As organizations grow and evolve, their IAM needs also change. IAM solutions offer scalability and flexibility to adapt to changing business requirements and accommodate growing user populations, applications, and IT infrastructure. Whether deploying on-premises, in the cloud, or through hybrid environments, IAM solutions provide the agility and scalability needed to support the organization’s evolving needs and digital transformation initiatives.
Conclusion
Identity and Access Management is a fundamental aspect of cybersecurity and risk management for organizations operating in today’s digital landscape. By implementing IAM solutions, organizations can enhance security, protect sensitive data, ensure regulatory compliance, improve productivity, and mitigate risks associated with user access. As cyber threats continue to evolve, IAM remains essential for safeguarding organizations against unauthorized access, data breaches, and other security incidents. Investing in robust IAM solutions is critical for organizations looking to build a strong and resilient security foundation and protect their digital assets now and in the future.